We’re all feeling the pinch when it comes to finding and retaining high quality talent. The reliance on skilled migrants and lack of opportunities in recent times is putting a strain on organisation’s Australia wide.
What has followed is the chaotic practice of talent poaching – particularly prevalent in local government departments, struggling to compete on an equal footing with big name consultancies operating without rigid and legacy structures and frameworks to offer game changing terms and benefits which are hard to resist.
As a practice, it’s not sustainable or ethical, and it’s causing previously unseen levels of vacancies in organisations across our country as ‘robbing Peter to pay Paul’ is becoming a normalised phenomenon in some industries and locations.
Either as the primary service or as a fail-safe backup, LEO satellites provide flexible, always-on network connectivity for essential services where alternative options like fibre or 5G are less viable or locations are off-grid or mobile.
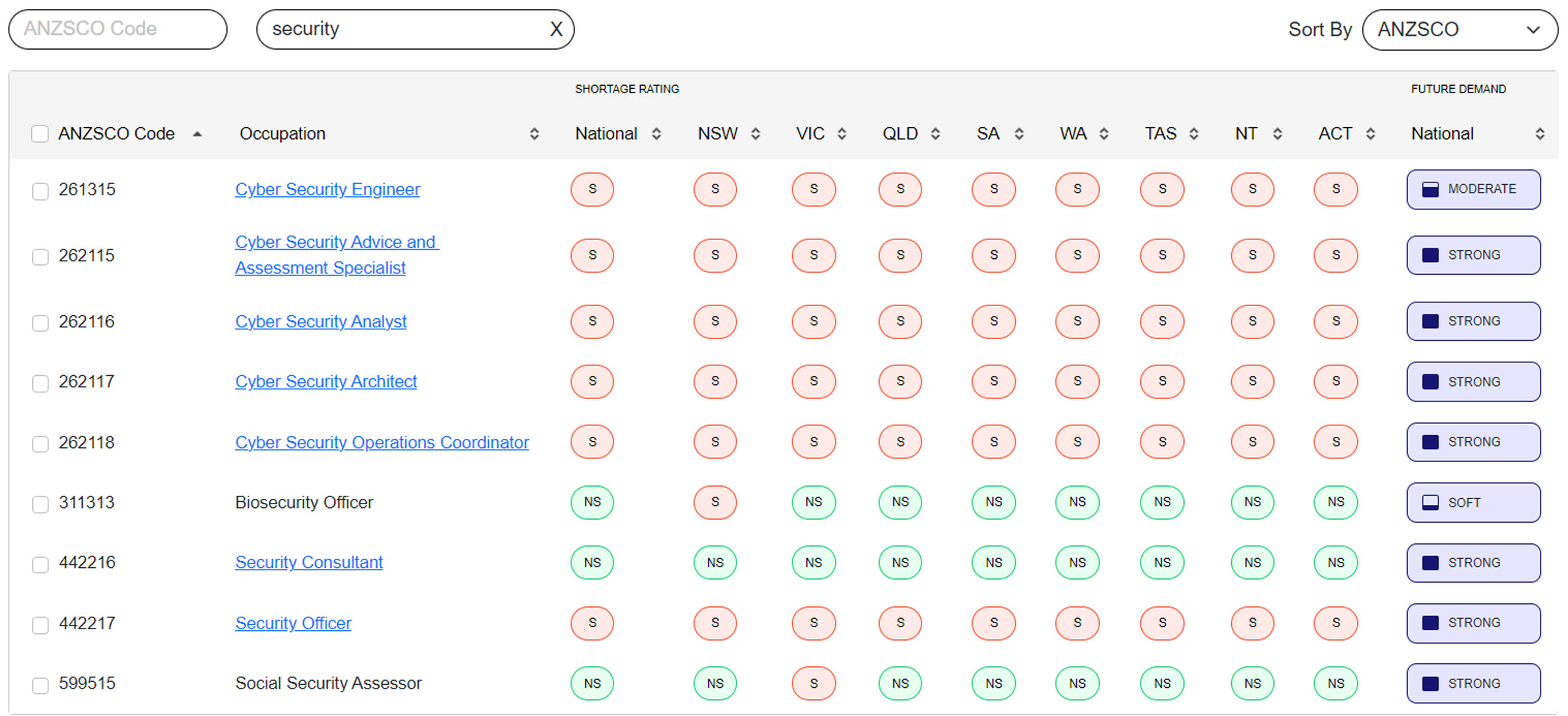
In the cyber industry, this is evidenced by the Skills Priority List (SPL) released by the Department of Employment and Workplace Relations (DEWR), showing further evidence of a tightening resource market, coupled with the forecasted future demand for ‘cutting edge skills’ , including significant demand for Cybersecurity skills in Australia and Singapore – it’s a trend set to continue for years to come.
Where to start?
Understand the role of cybersecurity in digital transformation
The buzzword bingo around digital transformation continues at every level. Importantly, everyone’s journey is different, so stay focused on protecting your IP, digital and human assets with a robust cyber strategy and fully trained and qualified team.
Do you know how your security posture stacks up today? Do you understand the landscape of risks for your organisation now? Do you know who is able and how to safeguard your environment for today and tomorrow? It’s time to bring future proofing to the table – especially around cybersecurity.
Understand the strategic importance of cybersecurity
It’s time to move away from just focusing on tactics when it comes to information security. We’re seeing the risk agenda driving conversations at Board level rather than in IT departments. Organisations are finally beginning to understand that Cyber risk is business risk.
In 2022, the number of high-profile ransomware attacks affecting every day Australians has changed perspectives for good. And while the likelihood of a ransomware attack is low, the impact is beyond belief – so it’s not a business case, it’s an imperative.
Add to this the other range of cyber-attacks facing your front-line staff every day, every organisation and person is at risk. So, what is your cyber strategy? Who is doing what and when? How does it fit with your other Business Continuity Plans? If you haven’t already, add it to your list of priorities, now.
Consider automation in your game plan
There is no doubt that automation should be a consideration in your strategy. While people are definitely the human barometer in identifying when things “just don’t feel right”, a robust Security Automation and Response (SOAR) or Security Information Event Management (SIEM) solution can vastly increase efficiencies and motivation. To be clear, implementing an automated solution isn’t often about losing resources but more about applying their talent to higher value activities which automation can’t handle. Done well, it’s a win: win for everyone. Happier people, more interesting work, better retention, better protection.
Investigate team augmentation and outsourcing
The pressure to be protected is driving organisations to outsource Security Operations Centres to support risk and insurance demands. When retaining talent becomes an impossible task, the re-assurance of a fixed and repeatable cost to manage risk in a measured way is certainly a consideration and worthy of review.
Done well, a SOC can deliver:
- Cost savings – the cost of outsourcing SecOps is significantly lower
- Current skills – from the straightforward to complex issues, there’s nothing they can’t handle
- 24 X 7 X 365 coverage – providing ‘always on’ protection provides peace of mind that’s hard to beat
- Cutting edge technology – best in class protection without the never-ending investment
- Scalable support – hybrid and scalable solutions configured for your organisation
- Wide ranging experience – every day knowledge and visibility of threats you just can’t get internally.
Commission an independent review
Defining what happens next isn’t simply a matter of pushing in disparate technologies without due consideration and validation. What works for someone else, won’t necessarily work for you.
We can’t be specialists in all things all of the time. So, engage the help of a reliable technology partner to bring together all of the different pieces of your puzzle. It’s time to stop, reflect, plan and act to protect yourselves in a way that’s customised for you and independent of competing priorities, politics and dynamics.
Threats evolve, talent moves on, technologies change, make sure you stay ahead of the game with an independent technology partner who can provide the insights you need.
Want help understanding your security posture and risks? Talk to us.