
It’s hard to believe that we’re coming towards the end of January, and as Australia begins to hesitantly open up again, we’re facing unforeseen risks and opportunities all around us.
Our strategic priorities have always been focused on delivering greater value to our clients through extended coverage, capability, and resources. Last year, in acquiring Equate Technologies, we tackled one of the region’s biggest challenges, by harnessing, embedding, and extending our capability in cyber security, now available to all of our clients.
Together, Equate and Nexon bring together best-in-class, end-to-end solutions to help clients to proactively detect, prevent, and respond to threats. From augmenting existing teams, tools, and technologies, to outsourcing capability to our fully managed, 24/7/365 SOC (Security Operations Centre) for absolute reassurance of protection, our solutions are tailored to meet your needs.
By working to first map and evaluate security maturity, we reduce and mitigate risk by remediating vulnerabilities and reducing security incidents, to ensure your organisation has the necessary foundations and tools to be both forewarned and forearmed.
Let’s start the conversation before you begin your planning and budgeting for the year ahead.
THE POWER OF TWO – NEXON AND EQUATE TECHNOLOGIES
This undisputable power of our two complementary businesses:
- Provides visibility and control of the security lifecycle
- Manages identity and access challenges
- Optimises the protection of IP and assets
- Aligns security strategy with regulatory frameworks
- Reduces the risk of cyber threats
- Proactively predicts, detects, and responds to risks and opportunities
- Ensures availability, accessibility, and integrity of data and systems
- Provides continuous improvement and system monitoring
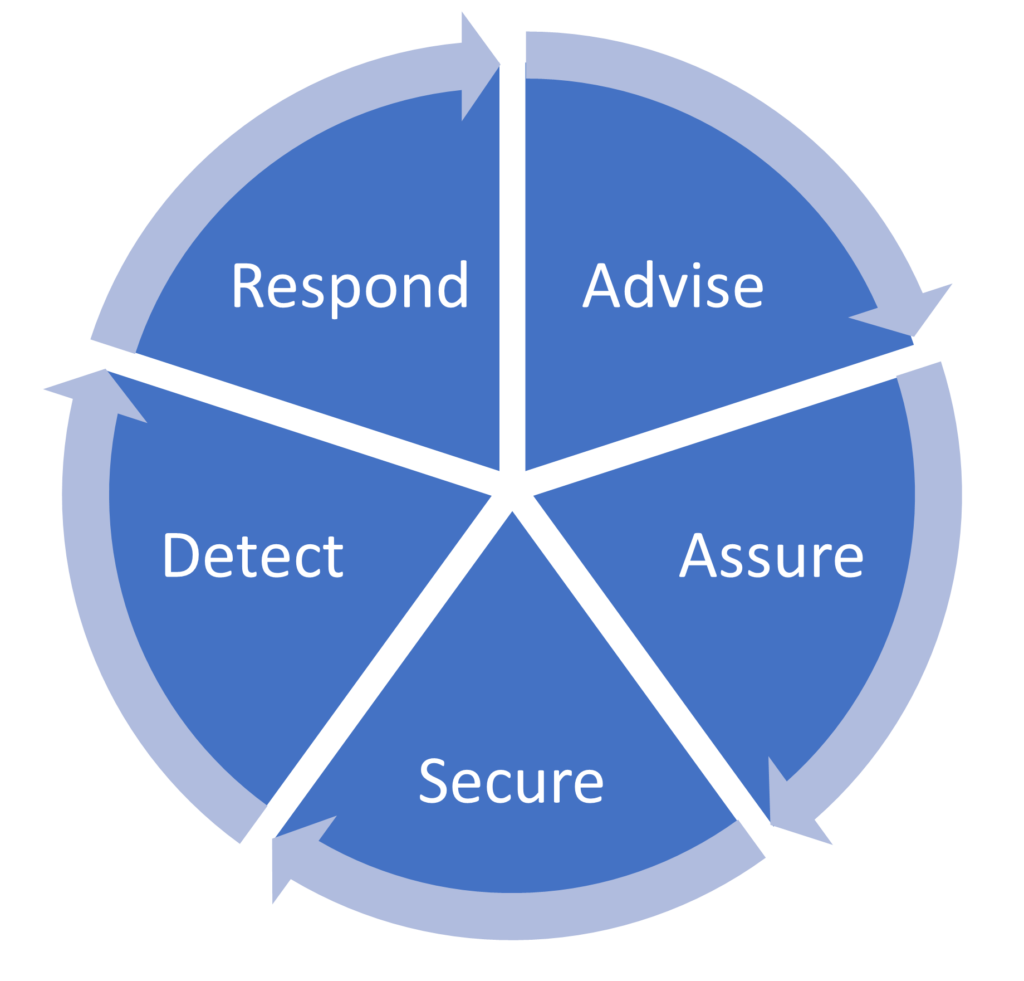
OUR SECURITY SERVICES LIFECYCLE
Our Services split across five key areas:
Advise: We work with you to understand and define security needs and future requirements; ensuring opportunities to secure and protect organisational assets are optimised from strategy to delivery.
Assure: We undertake independent testing and incident simulations to ensure networks and applications are secured, and teams are equipped and able to respond with minimal disruption in the fastest timeframe.
Secure: We design, define, deploy, and optimise information security solutions that improve performance, productivity, and protection for organisations and provide a secure and sustainable future.
Detect: We collect and correlate events from security infrastructure, network, and endpoints in order to detect, manage, and process vulnerabilities and alerts, prioritising and actioning remediation activities to re-secure environments.
Respond: We provide scalable and modular support for our clients, ranging from augmentation of security capability to a fully managed service. Our incident management capability is focused on remediating security breaches, SecOps automation and Security Incident Response.
This solutions wheel provides a greater insight into the modular services and capability we offer.
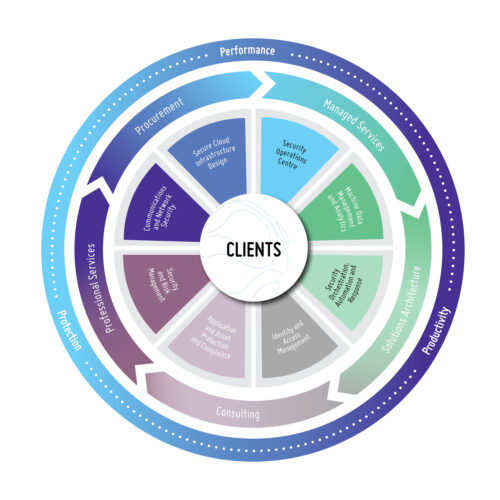
For more information or to organise your initial security maturity evaluation and consultation, contact us today.