
You will no doubt have seen the escalating news about the latest Microsoft Outlook vulnerability (CVE-2023-23397). If you have and ignored it or if you haven’t seen it, please keep reading to understand what it is, what it means for your organisation and what you can do to protect yourself and organisation quickly and easily.
What is CVE-2023-23397?
It is a Zero Day (Critical) vulnerability within Microsoft Outlook which can expose your password hash to attackers. Once your password hash has been stolen, attackers can do things like crack your password and then use it to login to other sites and applications appearing as you (the user).
What is particularly challenging with this vulnerability is its ability to infiltrate Microsoft Outlook without you even having to open an e-mail or click on an embedded link. So, if you’re targeted and your system is not up to date, there’s potentially trouble ahead.
How critical is CVE-2023-23397?
Rated 9.8 /10 on the Common Vulnerability Scoring System, this vulnerability it is extremely critical, so if you think you are at risk, read on to find out how to fix it.
What action can you take?
In simple terms, update your system. This will remediate the vulnerability immediately.
Microsoft has released an update to the Microsoft Office application suite for users to install.
Your ability to update Microsoft Office, however, will vary based on which policies your IT provider has enforced.
To check if you can update your own Microsoft Office applications – from within any application (Word, Excel or Outlook) follow these instructions:
On the ribbon, click on File.
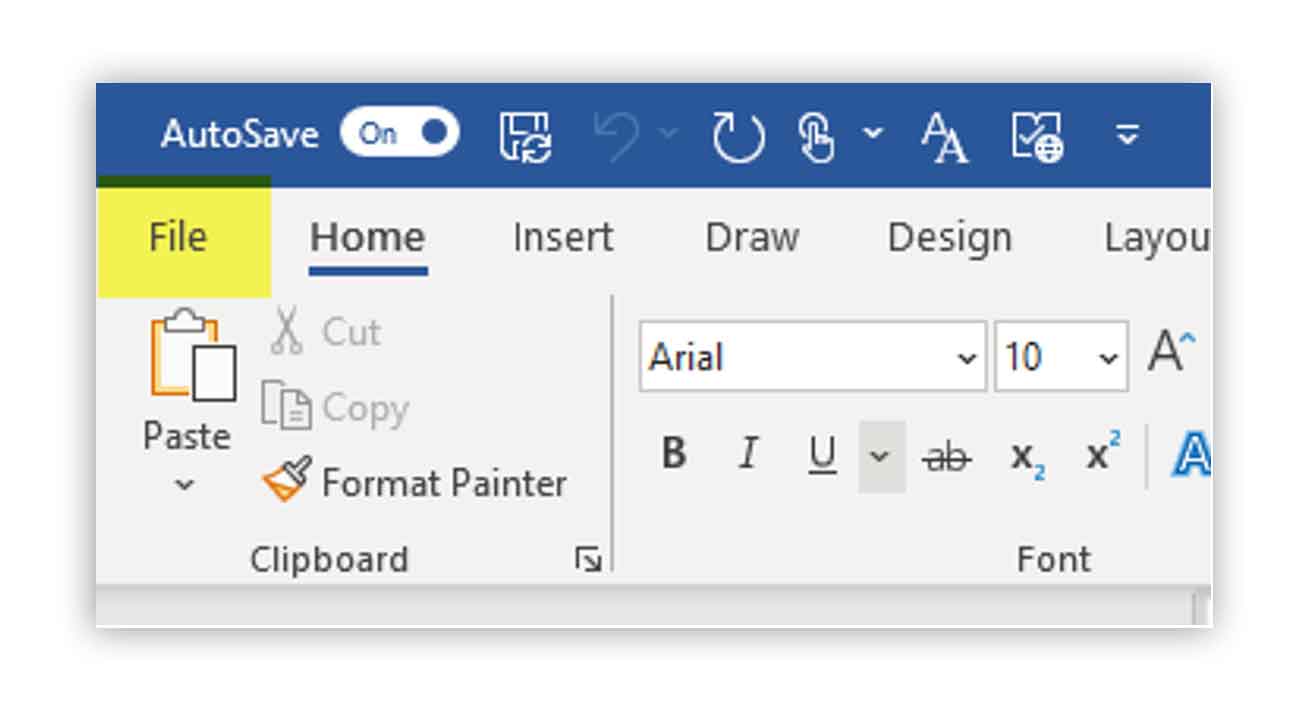
Look to the bottom left and click on Account
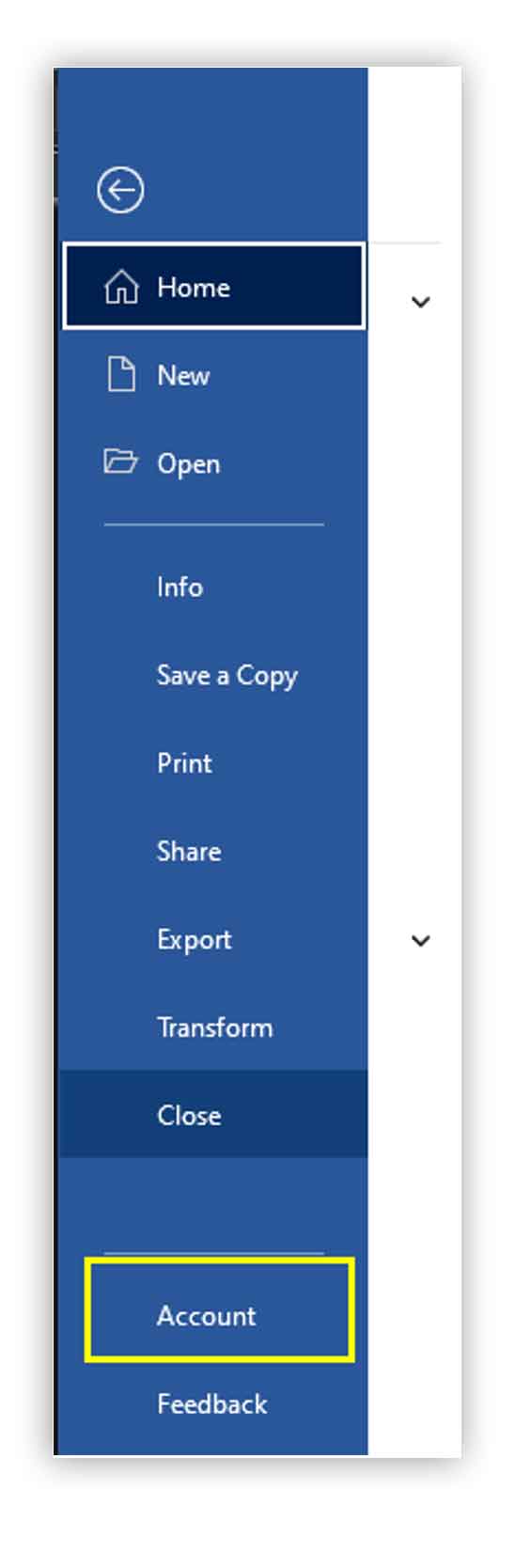
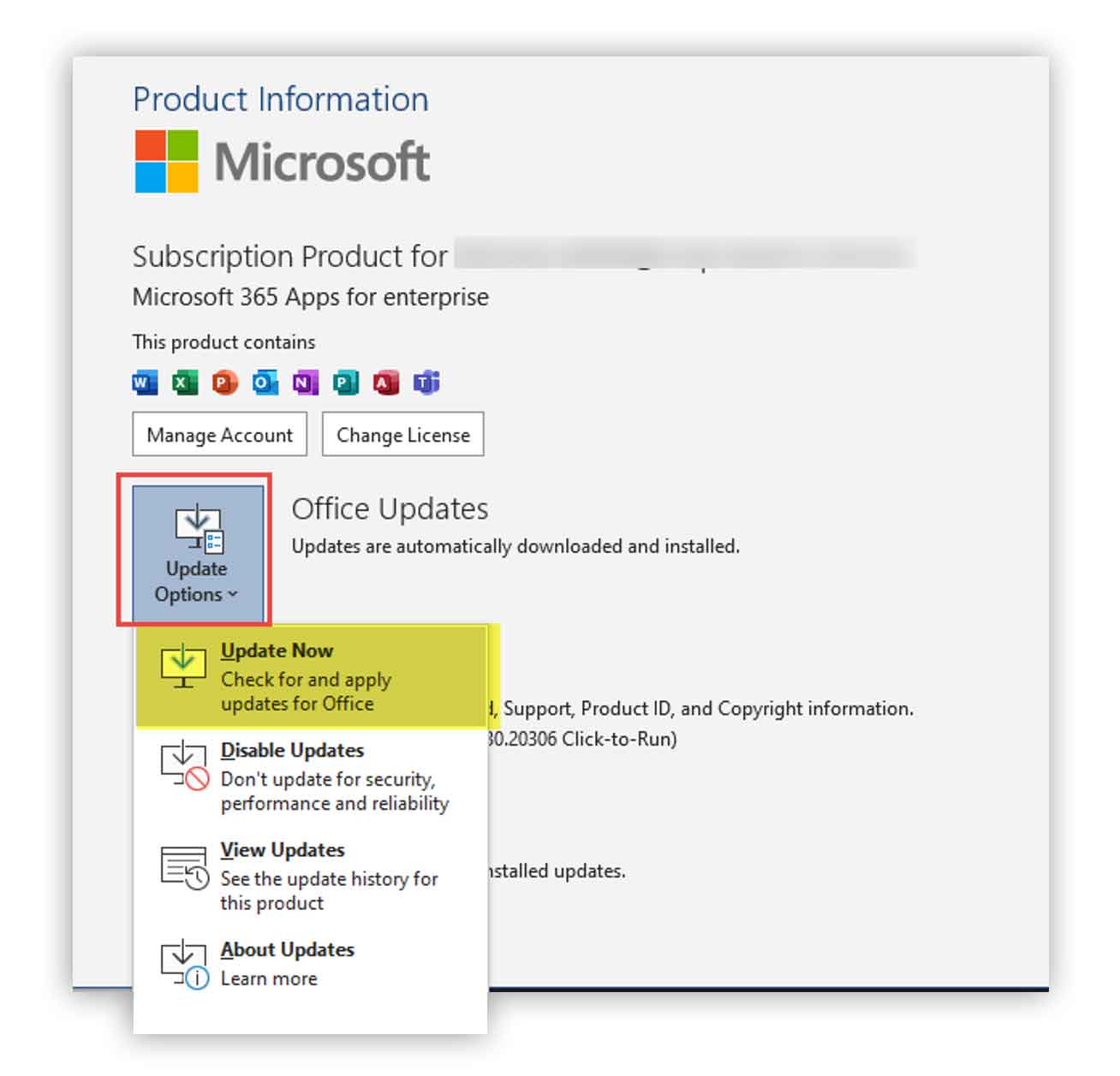
Look over to the right and click on Update Options. Then click on Update Now
Office will then automatically update, and this will take 5-10 minutes to complete.
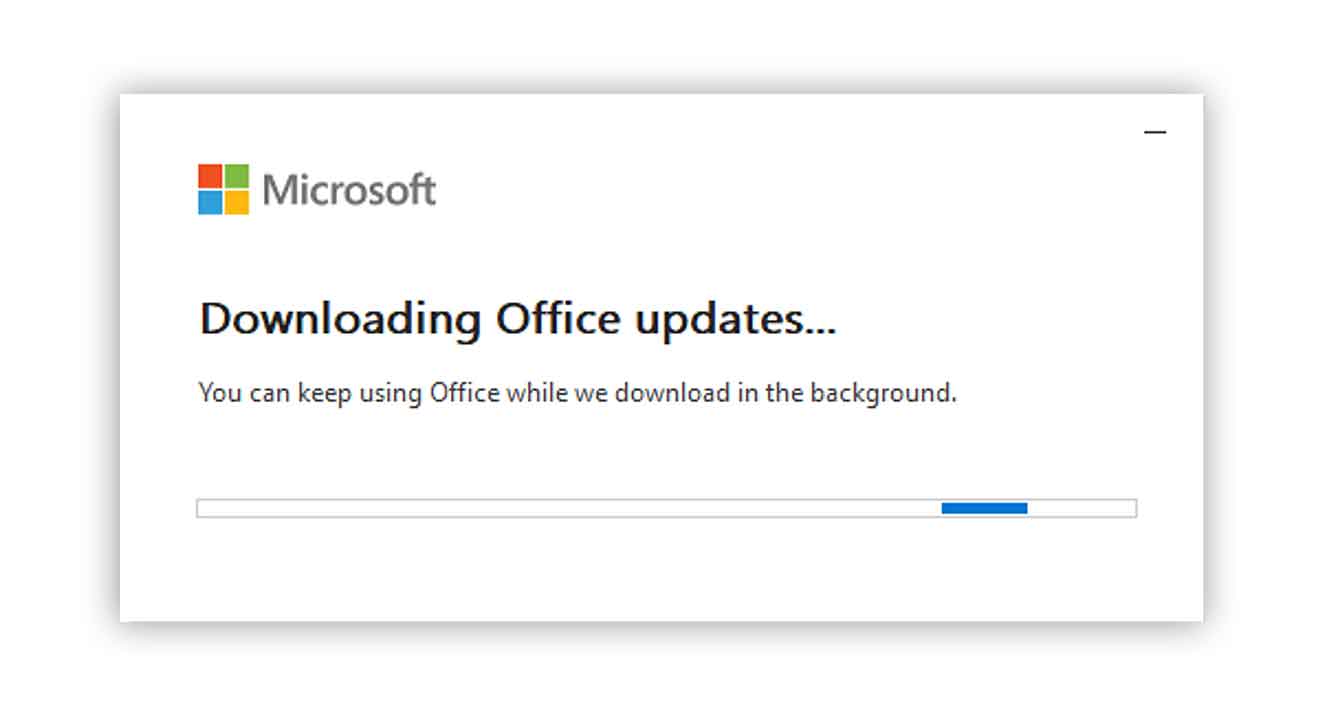
You may have to save your work and restart your applications.
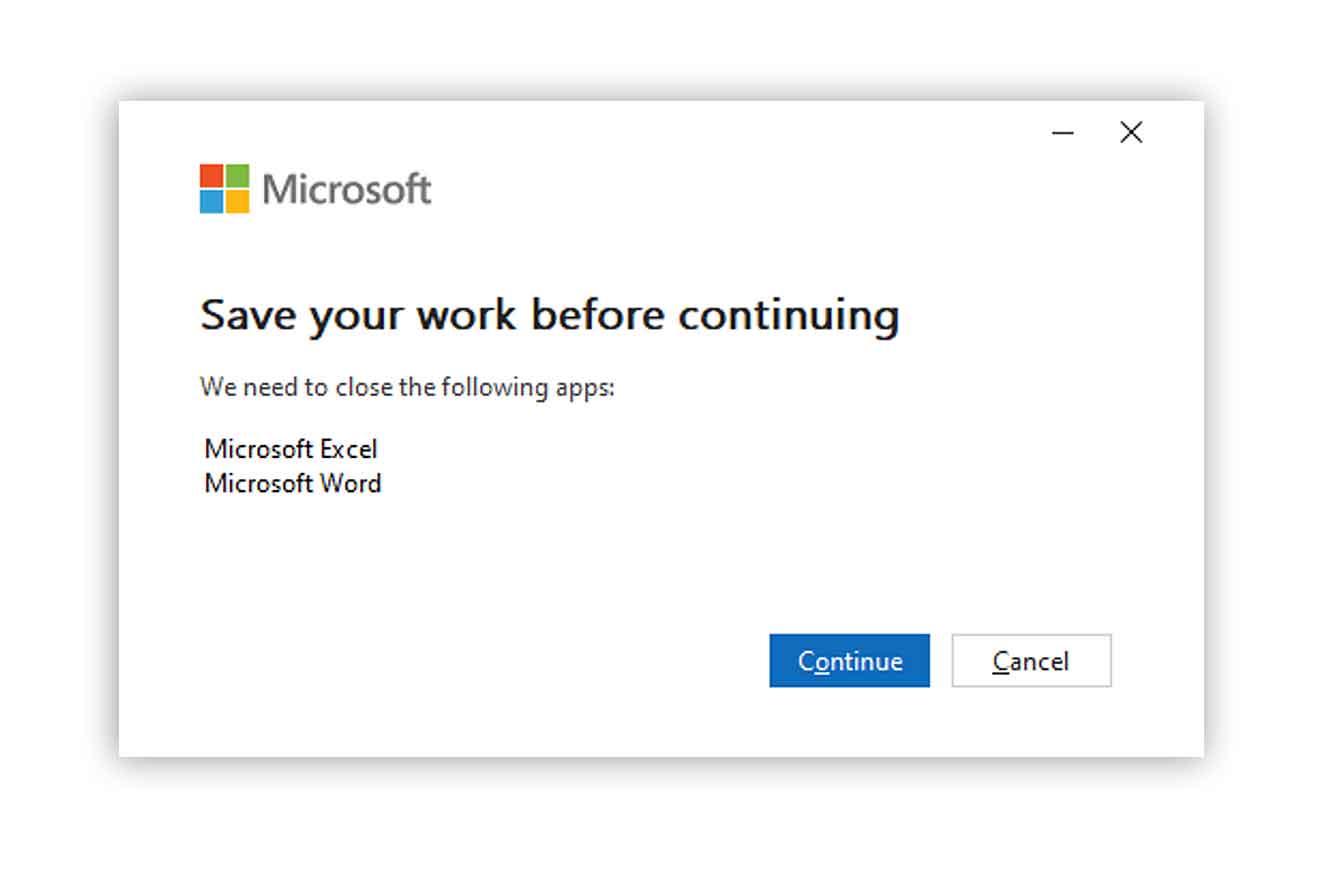
When the update is complete, your system will be up-to-date and protected from this vulnerability.
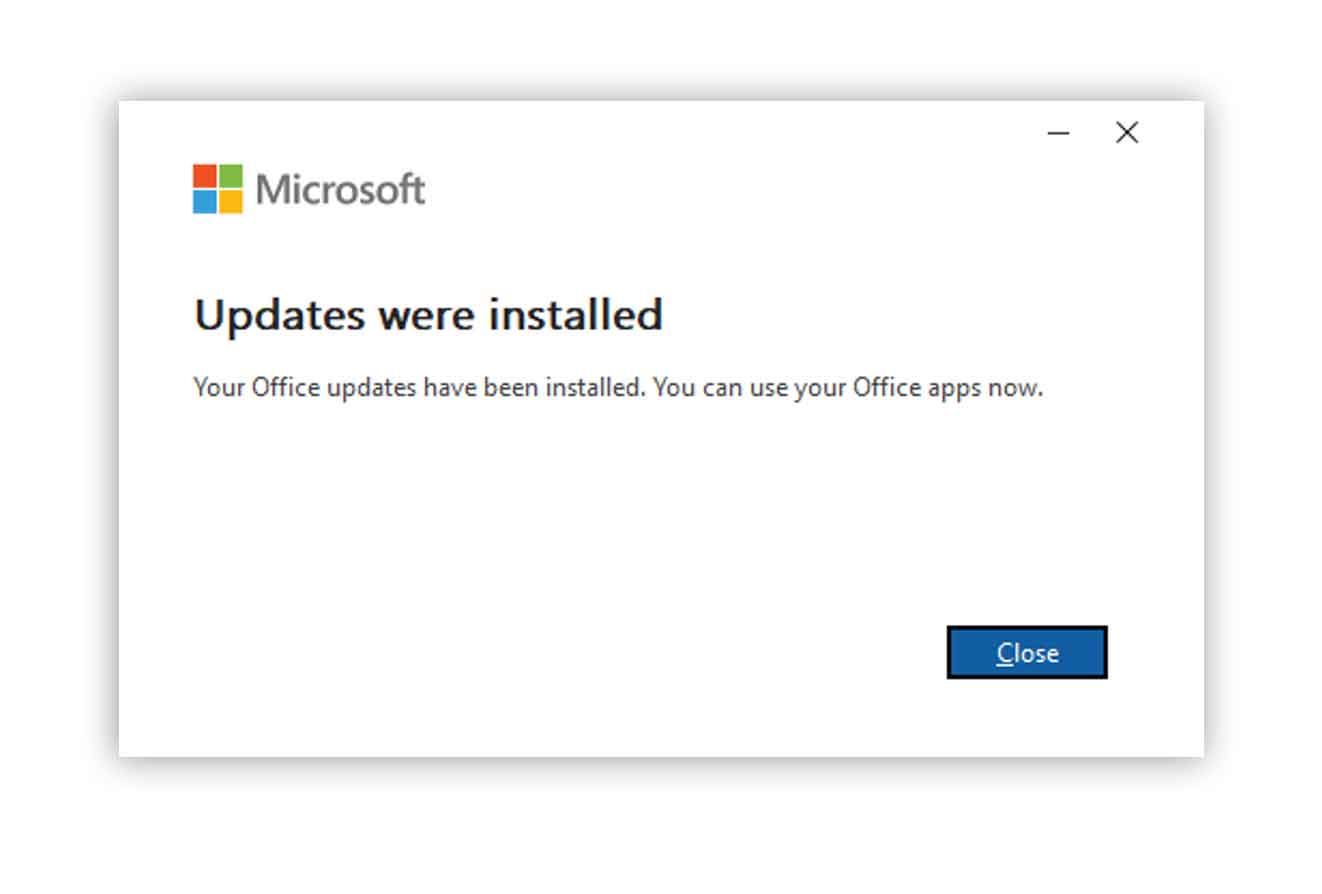
NOTE:
If you are unable to click on “Update Options” or you are missing the “Update Now” button shown above, your IT provider is likely controlling your ability to update Microsoft Office.
In these cases, please connect with your IT Services provider and ask them to push through the latest update or contact us for support and assistance.
We also recommend implementing a regular Microsoft Office update schedule, so that your computer is regularly receiving the latest security updates and new features.
Our final recommendation
It’s extremely straight forward.
1 – Take immediate action – update your Microsoft Office software as soon as you can.
2 – Talk to us for advice or support – we are here to help.